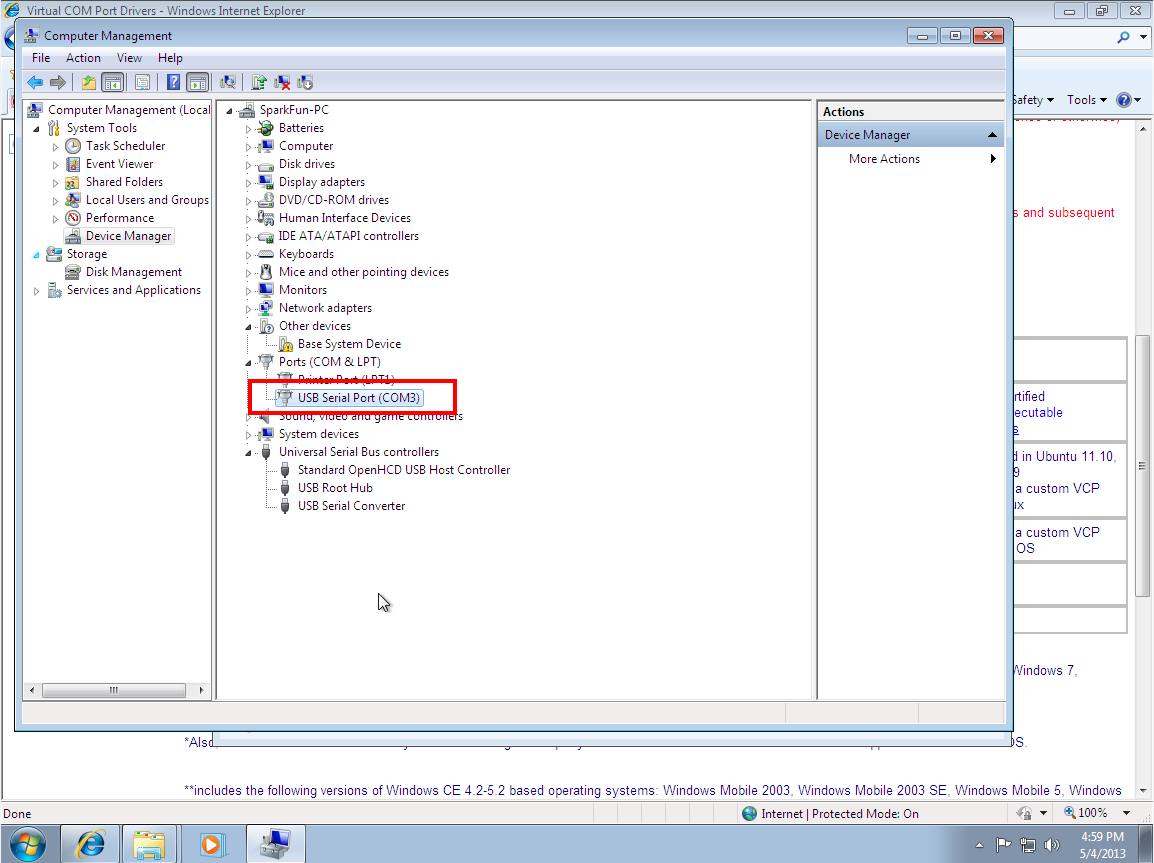
Ubuntu Serial Port Sniffer Cable
Serial Port Debugging on Ubuntu. The termios settings that are getting set on the serial port handle at. To embedded Linux / BSD device via null modem cable. Jan 20, 2015 - Minicom is a text-based serial port communications program. It is used to talk to external RS-232 devices such as mobile phones, routers,.
Is a tool to connect (nearly) everything to (nearly) everything, and can duplicate streams. In your usecase you could connect your serial port /dev/ttyS0 to a PTY /tmp/ttyV0, then point your application to the PTY, and have socat tee out Input and Output somewhere for you to observe. Googling 'socat serial port pty tee debug' will point you to several examples, one being: socat /dev/ttyS0,raw,echo=0 SYSTEM:'tee in.txt socat - 'PTY,link=/tmp/ttyV0,raw,echo=0,waitslave' tee out.txt' The files in.txt and out.txt will then contain the captured data.
This has been confirmed to work by commenters (@ogurets).
I am running VirtualBox under linux. Gues OS is Windows XP. I have an IR transmitter connected to serial port, (yes the old kind ), on my box and added the following in VirtualBox 'Serial Ports': [v] Enable Serial Port Port Number: COM1 IRQ: 4 I/O Port: 0x3F8 Port Mode: Host Device Port/File_PAth: /dev/ttyS0 Added user to group for serial. Vnvolchkova stepanova konspekti zanyatij vo vtoroj mladshej gruppe. Now: I am using sniffer on host; ie jpnevulator jpnevulator --ascii --timing-print --tty /dev/ttyS0 --read Run Guest OS and start IR software and write data by IR (In guest OS/WinXP).
The data is written, but nothing comes up in jpnevulator. What am I missing here? After a lot of testing in a field I am a pure novice I found the following way to monitor traffic: In VirtualBox 'Serial Ports': [v] Enable Serial Port Port Number: COM1 IRQ: 4 I/O Port: 0x3F8 Port Mode: Host Pipe Port/File_PAth: /tmp/vbwincom1 And then use socat /tmp/vbwincom1 - Data written to pipe is written to terminal in host linux.
This is by monitoring socket instead of serial. If anyone have a solution for monitoring /dev/ttyS0 instead of an overlayer by socket I'll accept that as an answer - but for now this does it.
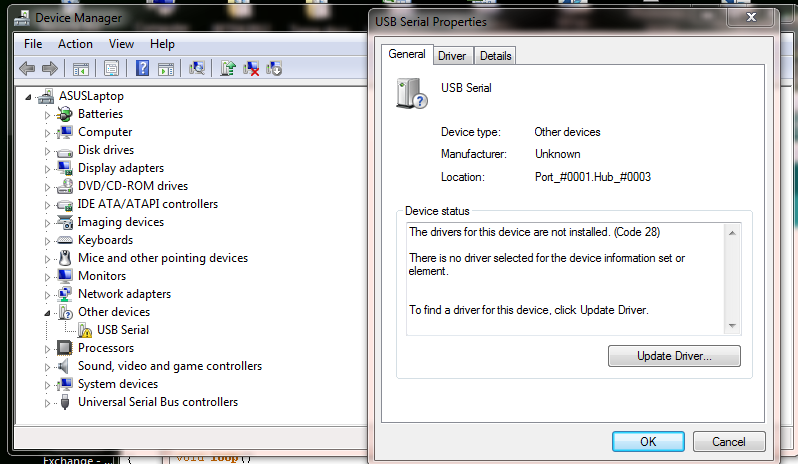
Hopefully it might help someone else.